Monitoring & Troubleshooting
Monitoring your user synchronization
Azure provides logs and tools to monitor user synchronization to Bizagi, offering the following options:
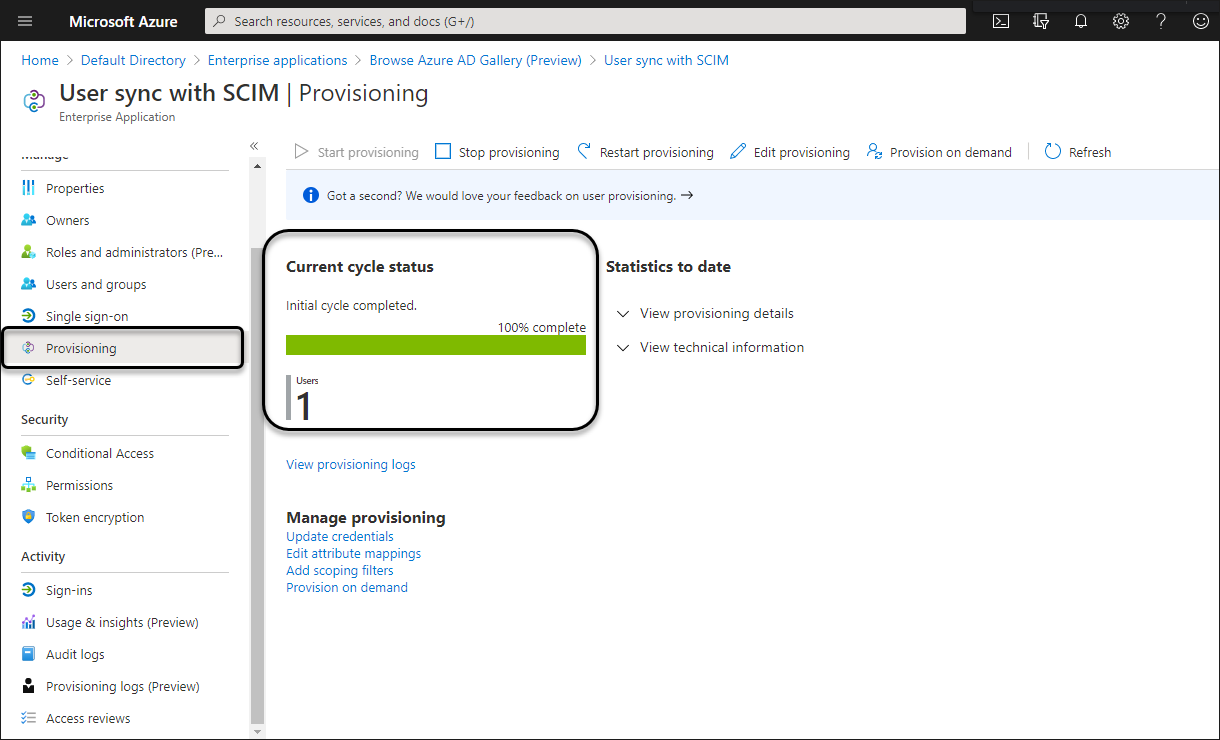
Progress Bar
You can review the provisioning progress bar:
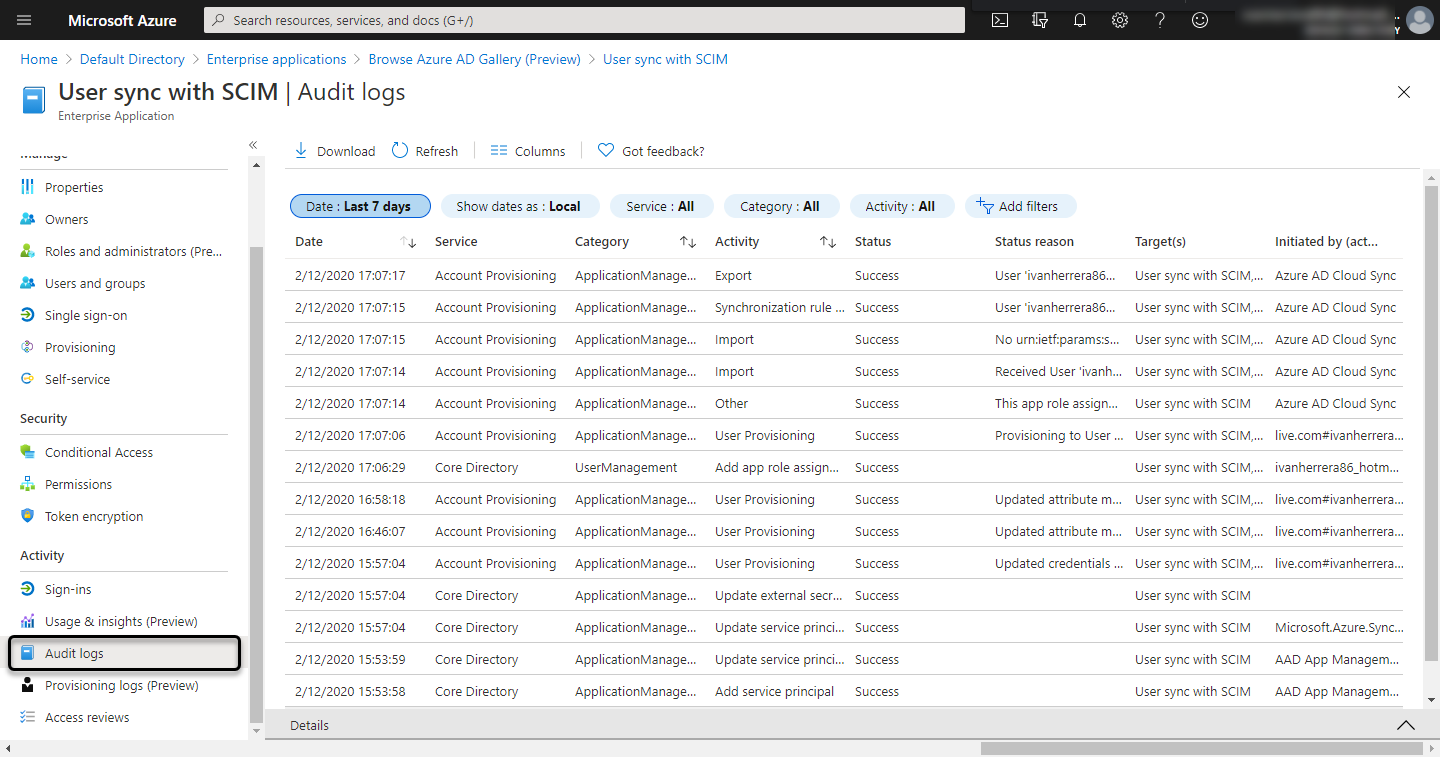
Audit logs
See the audit log of the provisioning options:
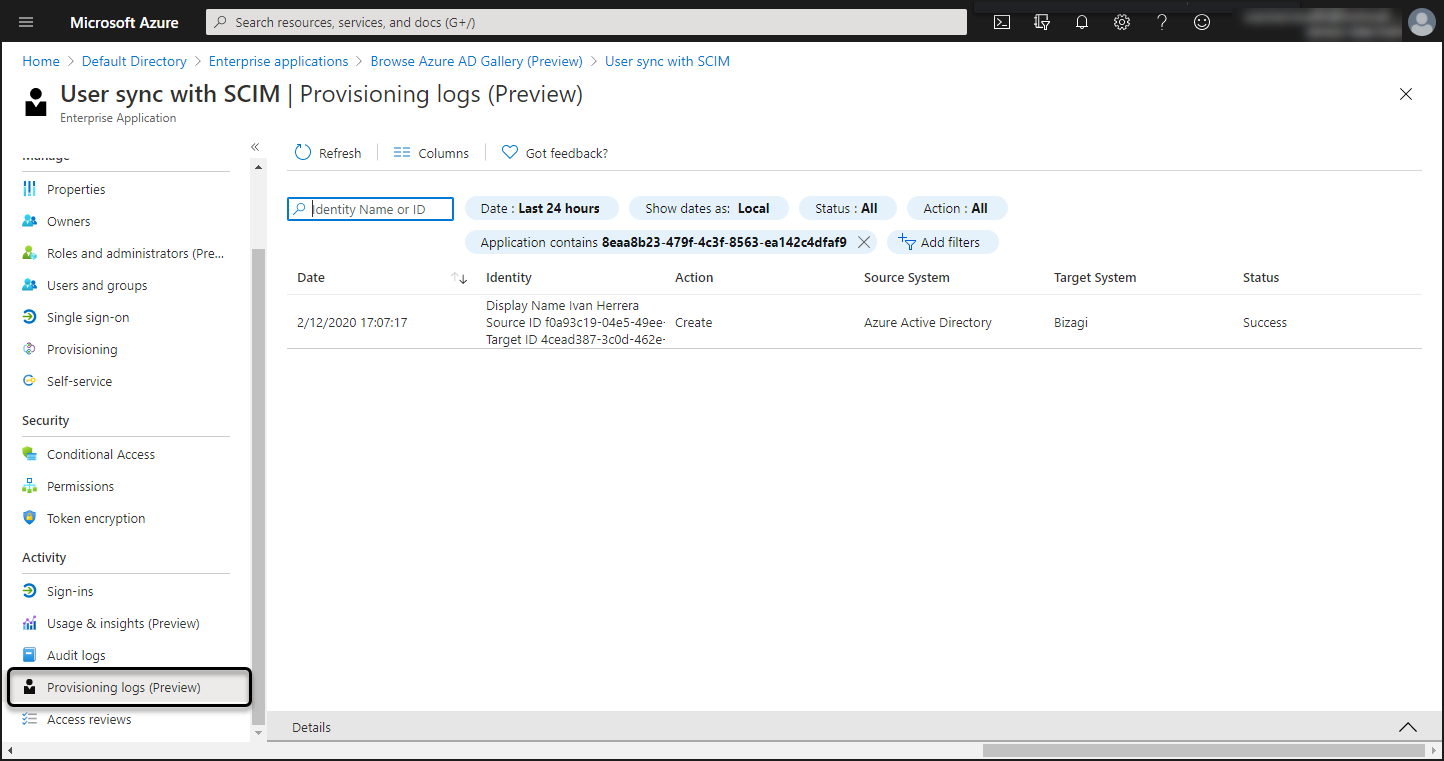
Provisioning Logs
You can review the Azure AD provisioning logs. For further information click here.
Troubleshooting
I can't read or provision a user - Error AADSTS50105 - The signed in user is not assigned to a role for the application
This incident occurs because Azure AD can only read and provision users that are immediate members of an explicitly assigned group. Therefore, the user must be assigned directly to the application. Also, you can use scoping filters to define attribute-based rules that determine which users are provisioned to an application.
I have noticed some users are not being synchronized
Azure AD handles its own cache memory. If you have issues, and some users are not being synchronized (specially after changes in your Development or Test environment), we recommend to delete the application in Azure AD and create it again.
For further information about error synchronization in Azure AD, check the article Understanding errors during Azure AD synchronization from the Microsoft documentation.
An error message was displayed, where can I look up for further information about it?
You can find AADSTS error descriptions, fixes, and some suggested workarounds in the Azure AD Authentication and Authorization Error Codes article from Microsoft's official documentation. However, since errors and messages are subject to change, check the instructions in the Lookup current error code information section.
What to do if my application is paused or under quarantine?
This error is generated when the assigned time in the Token lifetime property has expired. When this happens, the application throws an error message indicating that the application is paused and has problems accessing the token. To avoid this, assign a value of 0 to this field during the bearer token generation.
Considerations
- Groups and roles synchronization is not supported.
- To deactivate users, you need to UPDATE the user information and set the Active attribute as false.
- Azure uses a cache memory that stores the users created using Azure AD with SCIM. These users are considered as "existing" users and, hence, therefore only they are updated after any user's information update. If a user is created manually in Bizagi (for example, from the Work Portal), this user will not exist in Azure's cache memory. Therefore, if you later include the user in the Azure Active Directory, it will be created as a new one because it does not exist in Azure's cache. However, this will generate a synchronization error as it already exists in Bizagi.